Mobile apps hottest IT enemy
Sanjee Balasuriya - MD and CEO, eCybersec Pvt Ltd
Mobile apps are the hottest thing in IT these days. They’ve rapidly
emerged for a range of constituents including the enterprise, consumers,
sales reps, boards of directors- and even infants. In the last 12 months
alone, more than 400,000 mobile applications have been launched, and
many of them were created by marketing teams not engineering groups. All
of this means that security professionals need to be savvy about the
threats they pose. We’ll examine the three key layers that make up a
mobile application, along with the top ten mobile app vulnerabilities
that have surfaced in the last two years.
What are mobile apps?
A mobile app is software that runs on a handheld device (phone,
tablet, e-reader, iPod, etc.) than can connect to Wi-Fi or wireless
carrier networks, and has an operating system that supports standalone
software. Usually, when people hear “mobile app” they assume you mean
native app. This is a program that runs on a handheld device (phone,
tablet, e-reader, iPod Touch, etc.) which has a “smart” operating system
which supports standalone software and can connect to the internet via
Wi-Fi or a wireless carrier network. Usually people download native
mobile apps from app stores such as the Apple app store or the Android
Market.
Challenges faced by developing secure mobile apps
Enterprises are increasingly transacting critical data with customers
and remote workers through mobile applications, yet the security of
these applications goes largely untested. Source code for mobile
applications is rarely available, as most software is written by third
parties, and is insufficient in finding vulnerabilities such as
backdoors, malicious code or flaws introduced by third party libraries
and components.
Having said this The Open Web Application Security Project (OWASP)
has released latest Top 10 Mobile Risks as follow,
 * Insecure Data Storage * Insecure Data Storage
* Weak Server Side Controls
* Insufficient Transport Layer Protection
* Client Side Injection
* Poor Authorization and Authentication
* Improper Session Handling
* Security Decisions Via Untrusted Inputs
* Side Channel Data Leakage
* Broken Cryptography
* Sensitive Information Disclosure
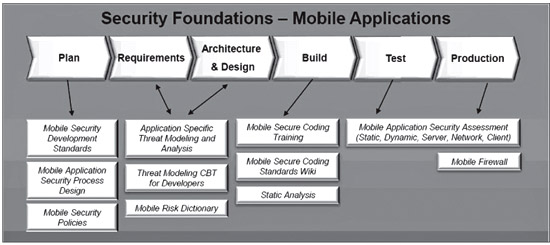
Just to give an overview of the Mobile Application Security
Fundamentals how it really works
What eCybersec can bring to the Sri Lankan Secure Mobile Application
Developing Market
First time in Sri Lanka eCybersec offers Mobile Application Security
Assessment Services to various verticals. We are partner with Veracode (
www.vercaode.com) who is the leading Mobile Applications Security
Testing Company in United States and provide automated static and
dynamic application security testing software and remediation services.
Presently we are in vital discussions with Sri Lankan leading mobile
apps developing software companies and how they could benefit our Mobile
Application Security Testing Assessments Services to write secure coding
to prevent such cyber attacks via mobile apps.
Even few leading banks in Sri lanka is moving in to mobile apps space
having own Internet banking app which consumers can use it and perform
all banking transactions while rather not logging in to normal internet
banking web site. Security will be a key aspect and banks need to
consider and we as a security consulting company glad to help in this.
Final Thoughts
The state of software security continues to be unnerving as
traditional perimeter defense and detection software are proving
woefully inadequate in the face of continued data loss from criminal and
hacktivist attacks. The attacks target weak applications that have been
built with extremely weak little to no security testing integrated into
the development lifecycle. We do not need more security software.
What we need is more secure software. In response, organizations are
putting in place comprehensive application security programs to deliver
more secure software.
These programs seek to instill application security best practices
and methodologies within their software development lifecycle (SDLC),
their outsourced development contracts, and their processes for
purchasing third-party software. |







